Dear readers,
Seven days have passed away since election day; and I am here to tell you to fight for the Kamala Harris & Tim Walz White House Administration that our country so vitally needs in order to protect our freedoms, liberties, and lives; yes it has come to this point in time now where any honest and objective examination of our immediate period of time since the fifth-of-November should yield the unwelcome and alarming realization that potentially millions of lives are at stake if Harris voters do not take a stand against a clearly and obviously criminal regime on a collusion course to their private black house.
The fifth-of-November that sounds so tailor-made, so V-like. I wonder what Elon provided for the plebeians in return for the data that would be so necessarily helpful and so easily gained from the most gullible morass of morons ever to think that they understood their Vote, via the technology $.trapped to their hands.
I most certainly understand my Vote and even more importantly my patriotic self-appointed duty to defend my country against what may correctly, definitionally, ethically, and morally be declared a domestic enemy.
For the past week I have been researching, investigating, reading, thinking and now I can say I am starting to see a pattern emerge.
Now what follows this opening statement is intended to be an antidote, an antitoxin, and an antibiotic against all the Main Stream Media and Legacy Press attempts to maintain command and control of the election narrative of an election that is far from over.
I. Have. So. Very. Much. To. SAY!
…but not right now;
97-percent of everyone vocalizing their opinions, perspectives, stories, tales, unicorns and zebras, et. al. need to STOP.
The following material is as serious as serious can get.
Because of all the garbage being cast at Democratic voters by everyone working so hard to deny us “our” election concerns and because so many Harris voters are already showing so much weakness in the face of an only just now fully emerging situation (Oh Yes, there is definitely significant activity underway and accelerating) shame on you, the remainder of this essay is in coloring book form.
Enough with the naivety, smarten up.
[Edited to add the following important related post]
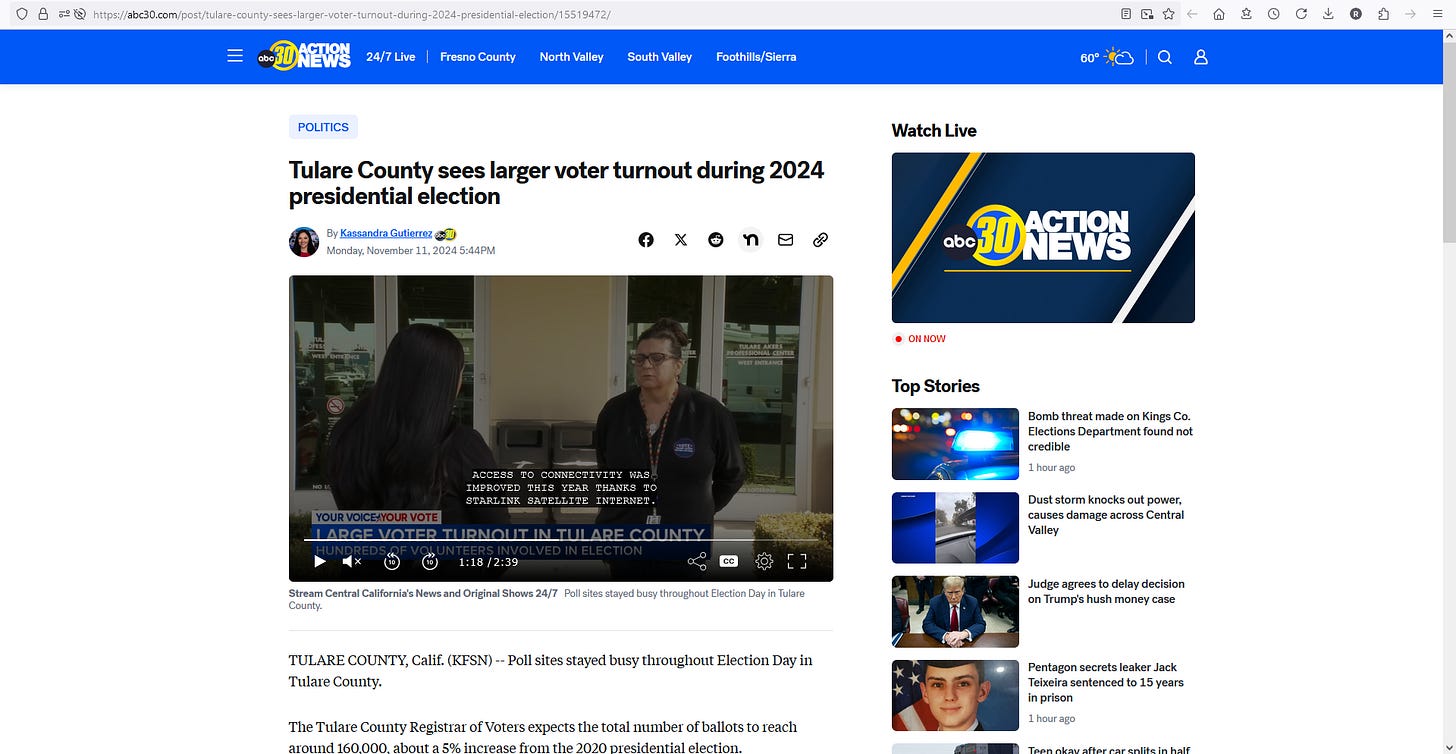
Tulare County Registrar of Voters Michelle Baldwin.
Baldwin says access to connectivity was improved this year thanks to Starlink satellite internet.
"Our laptops and our connectivity, that worked really well. In 2020, a lot of problems we experienced were due to slow connectivity at our polling places. We purchased Starlink for our sites, so as far as the connectivity that worked was awesome," says Michelle Baldwin.
She adds early technical difficulties with a tabulator machine were quickly fixed and did not impact the vote count.
Five of the ten volunteers assigned to the Exeter poll location did not show up, but Baldwin says this site processed 1,263 ballots, compared to the 831 ballots in 2020.
“THE LAW”
A voting system shall comply with all of the following:
(a) No part of the voting system shall be connected to the internet at any time.
(b) No part of the voting system shall electronically receive or transmit election data through an exterior communication network, including the public telephone system, if the communication originates from or terminates at a polling place, satellite location, or counting center.
(c) (1) No part of the voting system shall receive or transmit wireless communications or wireless data transfers.
(2) A network connection to any device not directly used and necessary for voting system functions shall not be established. Communication by or with any component of the voting system by wireless or modem transmission at any time is prohibited. A component of the voting system, or any device with network connectivity to the voting system, shall not be connected to the internet, directly or indirectly, at any time.
https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=19205.&lawCode=ELEC
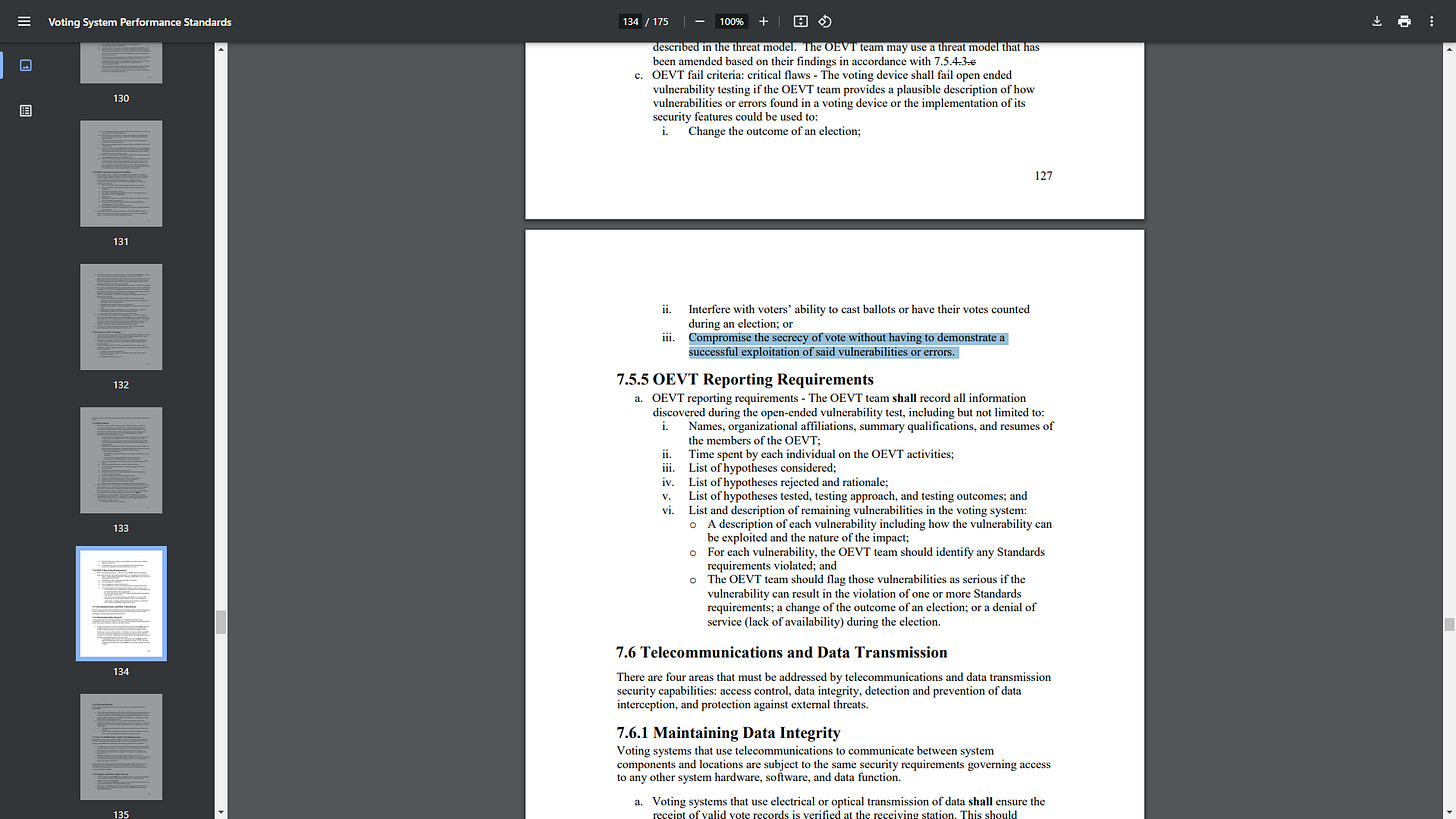
OEVT fail criteria: critical flaws - The voting device shall fail open ended vulnerability testing if the OEVT team provides a plausible description of how vulnerabilities or errors found in a voting device or the implementation of its security features could be used to:
i. Change the outcome of an election;
ii. Interfere with voters’ ability to cast ballots or have their votes counted during an election; or
iii. Compromise the secrecy of vote without having to demonstrate a successful exploitation of said vulnerabilities or errors.
https://admin.cdn.sos.ca.gov/regulations/elections/california-voting-system-standards.pdf
Voting systems connected to the Internet will be exposed to online attacks.
It is commonly accepted that voting systems should not be connected to the Internet. However, we should first consider what constitutes an Internet connection that could potentially expose vote data to an online attack.
There may be a perception that a vote counting or tabulating system must be continually connected to the Internet to expose it to online actor, or that the system must be connected to the Internet at the time the votes are being tabulated for the attack to be successful. It may be expected that a computer hosting an Election Management System (EMS) can be kept offline but networked to the local county network safely. However, if any devices on the local county network are connected to the Internet, this creates an exploitable Internet connection that could compromise the security of the EMS. It may also be expected that a voting system component which does not operate on the Internet - like the EMS – can operate safely offline while the same server hosts other programs and systems which do operate on the Internet. Finally, it is important to note that many computers which host the EMS are laptops which have wireless internet capacity installed which could make them vulnerable to online attacks. All of these situations create an Internet connection which could be exploited to compromise vote data.
If the EMS is exposed the Internet, it can be targeted and infected with malware intended to corrupt vote data. This malware can then be transferred [to] the memory cards configured by the EMS for use in the individual voting machines and optical scanners.
https://www.nist.gov/itl/voting/security-recommendations
Vulnerabilities of electronic voting systems
This section argues that there is a class of security flaws that so gravely undermine election integrity—and thereby, democratic legitimacy—as to outweigh countervailing interests, and that electronic voting is more vulnerable to such failures than paper-based alternatives.
We call these serious failures: situations where election results have been changed (whether by simple error or adversarial attack) and the change may be undetectable, or even if detected, be irreparable without running a whole new election.
Merely the fact and public perception that the system is vulnerable to such failures may reduce an elected official’s legitimacy and therefore destabilize a democracy. Vulnerability to serious failures thus undermines government legitimacy, whether or not the vulnerability was exploited by an attacker.
https://academic.oup.com/cybersecurity/article/7/1/tyaa025/6137886#333667671
(b) Voting system defined
In this section, the term "voting system" means-
(1) the total combination of mechanical, electromechanical, or electronic equipment (including the software, firmware, and documentation required to program, control, and support the equipment) that is used-
(A) to define ballots;
(B) to cast and count votes;
(C) to report or display election results; and
(D) to maintain and produce any audit trail information; and
(2) the practices and associated documentation used-
(A) to identify system components and versions of such components;
(B) to test the system during its development and maintenance;
(C) to maintain records of system errors and defects;
(D) to determine specific system changes to be made to a system after the initial qualification of the system; and
(E) to make available any materials to the voter (such as notices, instructions, forms, or paper ballots).
https://uscode.house.gov/view.xhtml?req=(title:52%20section:21081%20edition:prelim)
Is there any evidence that internet voting is secure?
No. Many credible cybersecurity experts warn that internet voting is unsafe and, if implemented, makes U.S. elections easy targets for attackers who seek to change election outcomes or sow distrust in our democracy.
Vulnerabilities exist and are very real especially at this point in time given how Donald Trump has entangled the White Christian nationalist businesses, forces, foundations, individuals, and organizations so deeply into the Grand-Old-Game with Putin’s Neo-Committee for State Security otherwise formerly known as the KGB.
'Online and vulnerable': Experts find nearly three dozen U.S. voting systems connected to internet
A team of election security experts used a “Google for servers” to challenge claims that voting machines do not connect to the internet and found some did.
I must repeat that the media and the press are manipulating the narrative to keep people from questioning the results.
We absolutely must question and investigate any and all discrepancies that have appeared and will continue to appear.
“Voting experts warn of ‘serious threats’ for 2024 from election equipment software breaches”
[Edited to add: The news story “Voting experts warn of ‘serious threats’” linked to immediately above is discussed in significant detail in the three letters sent to the Department of Justice and Vice President Harris that are the centerpiece of the following article “Election Security Investigation” please read it as it contains very important and vital need-to-know-information.]
My next essay will discuss “the Duty to Warn Letter” by Stephen Spoonamore [See ‘edit-note’ above] who is a bona-fide expert whose work has already previously exposed election fraud that took place during 2002. If he suggests that he has “suspicions of hacking” of election systems then he should be having direct conversations with the White House immediately; in the meantime we the people must take up a rallying cry to support our legitimate concerns and demands for the fullest assurances of an Election Security Investigation which is something that current circumstances more than merit.
These are issues of the gravest National Security concerns and hence it is no wonder that the Harris campaign is treading so lightly right now.
Thank you for reading,
Robert J. Rei November 12, 2024





















Hello Elizabeth. It has been some time since we have interacted. I would like to first correct the erroneous notion of the "Voting Machines" what America has now are Election Management Systems (EMS) of which there are myriads upon myriads of moving and static parts.
In order for the Starlink Internet Connectivity (SIC) to be present in the story that leads my article the SIC would have to by law be present and part of the California Election Management System Standards, the standards of which I provided multiple screen shots of and a PDF copy and a URL link.
There is quite simply zero questions about the reality and fact of the SIC being connected into the USA Election Management Systems.
Also consider Elon Musk's one-on-one relationship that they are no longer hiding away from the public. That is connection enough for me to start digging, as I have been for the past week now. I have a nascent theory rapidly blossoming in my mind. I am definitely seeing a pattern emerge.
On a closely related note I think that you will find the following item to be of interest to you.
"Trump to rely on forces that brought him to power — Russian presidential aide"
https://tass.com/politics/1870713
If you had taken the time to actually look at the material presented you would have seen that yes connectivity to laptops and the Starlink system does happen. As can be seen in this one quote from above in the California "Voting System Performance Standards under section 7.5.1 OEVT "Scope and Priorities" c. xiii, as follows:
"xiii. The OEVT team should not consider the voting device vulnerabilities that
require Internet connectivity for exploitation if the voting device is not
connected to the Internet during the election and otherwise. However, if
the voting device is connected to another device which in turn may have
been connected to the Internet (as may be the case of epollbooks), Internet
based attacks may be plausible and should be investigated. " (Page 131-PDF/125-Paper)
An epollbook as mentioned above is a laptop type of device.
And also further down in my "coloring book" is this warning from the National Institute of Science and Technology in a blunt statement about the fact that internet connectivity of Election Management Systems (EMS) is a fact and reality:
"Finally, it is important to note that many computers which host the EMS are laptops which have wireless internet capacity installed which could make them vulnerable to online attacks. All of these situations create an Internet connection which could be exploited to compromise vote data."